Tailor AI agents
to your team needs
Anyone on your team can create personalized agents.


Build agents with custom instructions and tools
Adapt instructions to your needs, with pre-built templates. Empower agents with specialized tools for data extraction, transformations, or advanced operations.


Feed your company context
Notion, Slack, GitHub, external websites (…) natively in minutes. Integrate anything via API.

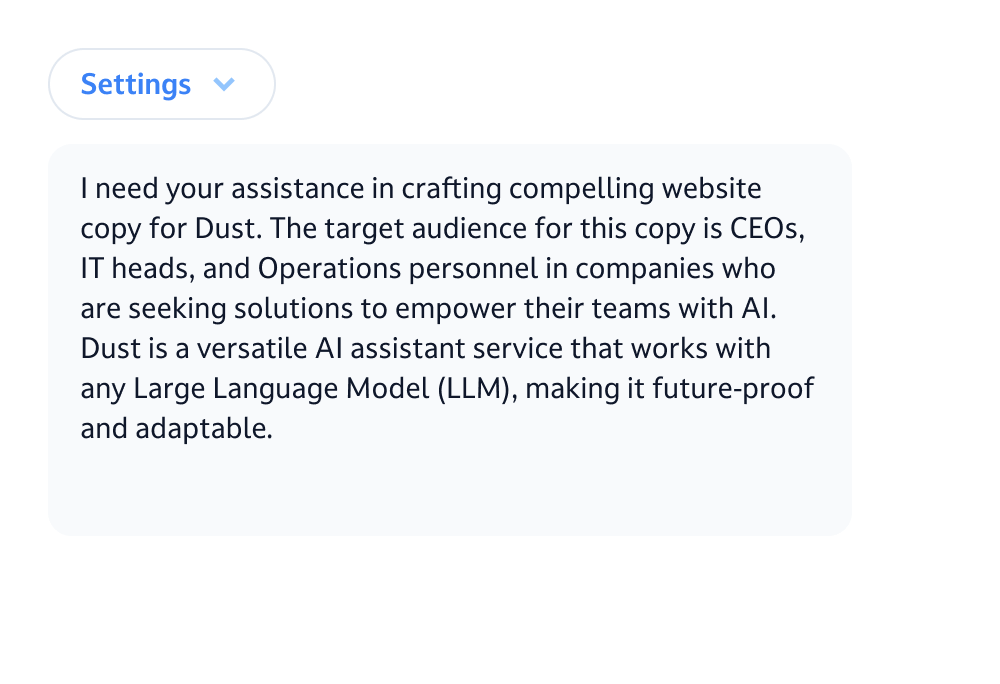

Leverage the best models on the market.
Choose OpenAI, Anthropic, Gemini, Mistral, or any cutting-edge model to ensure your agents stay smartest.
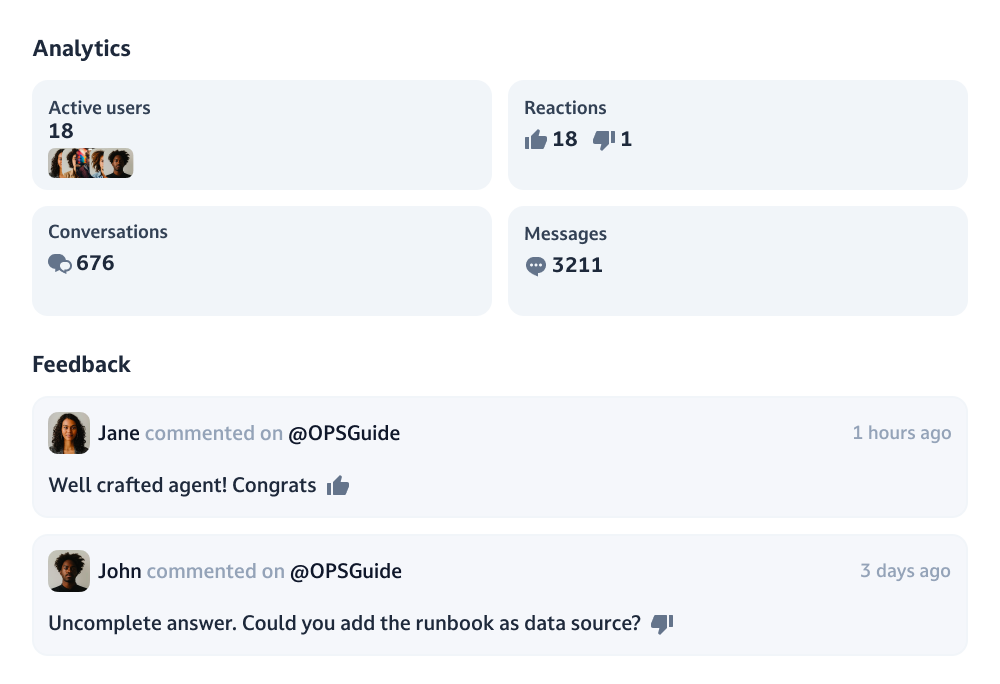
Share with your team, collect feedback
Empower tinkerers to build agents for their teams and get continuous feedback to iterate on them.
Dust in motion
Have AI wherever you work
Leverage the power of AI and your knowledge right where you need it.
No back and forth across tools.

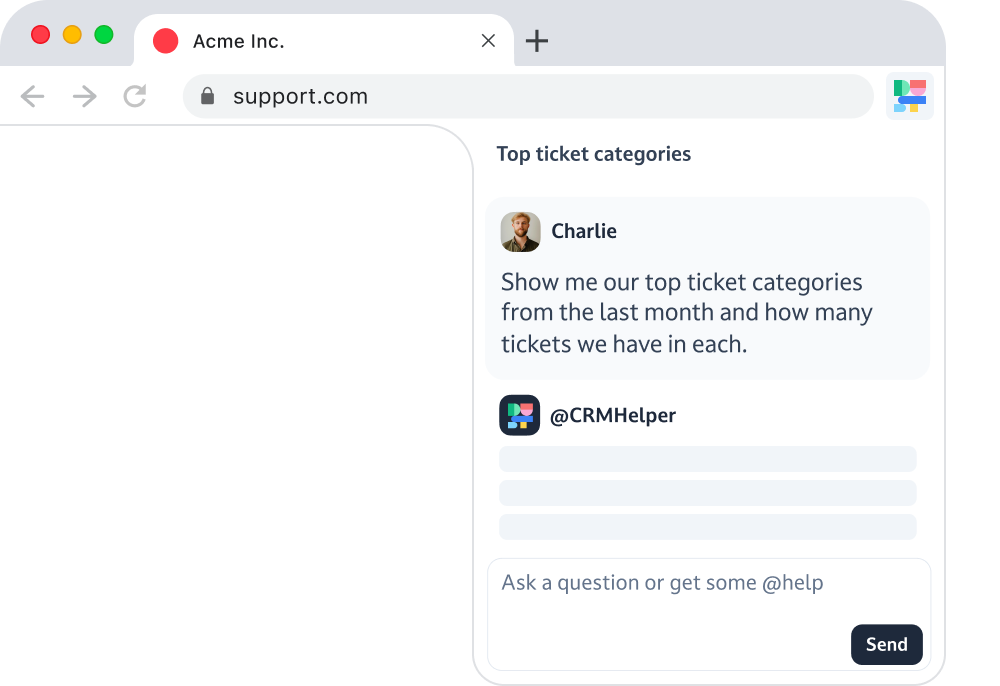
Use in your browser
Access Dust wherever you work via our Chrome extension—no app-switching required.

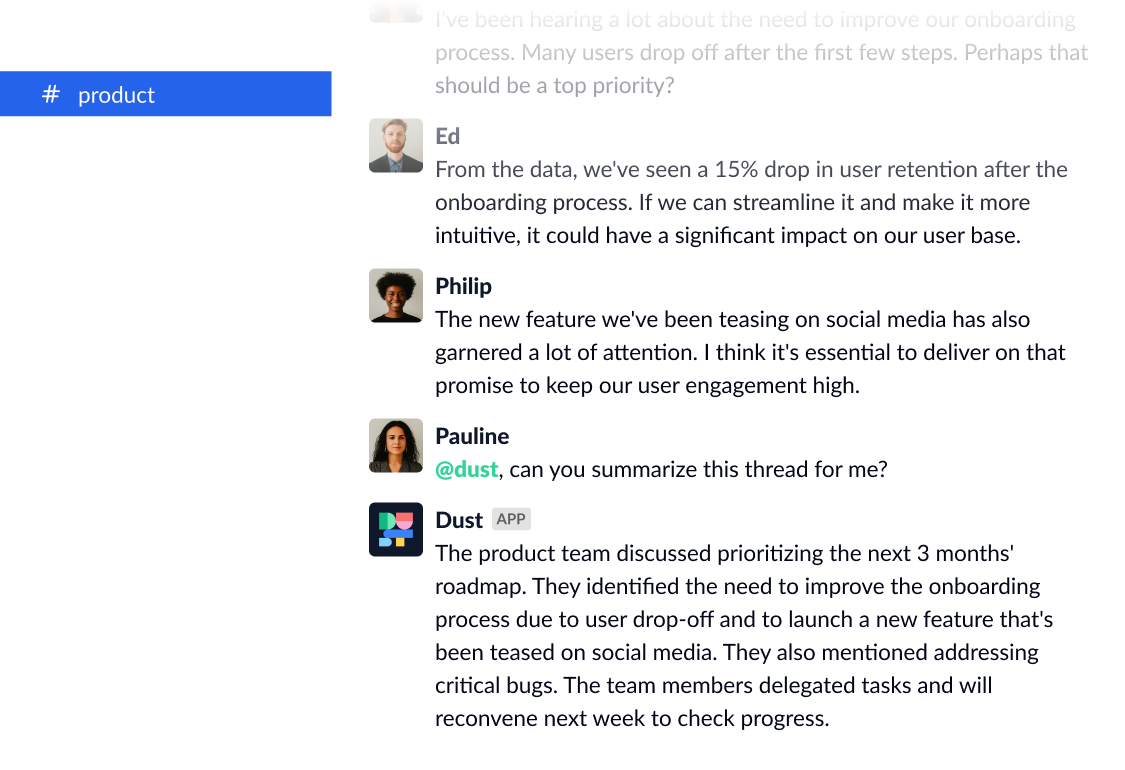
Access from your tools
Bring Dust's to Slack , Zendesk and others to bring Dust where you need it.
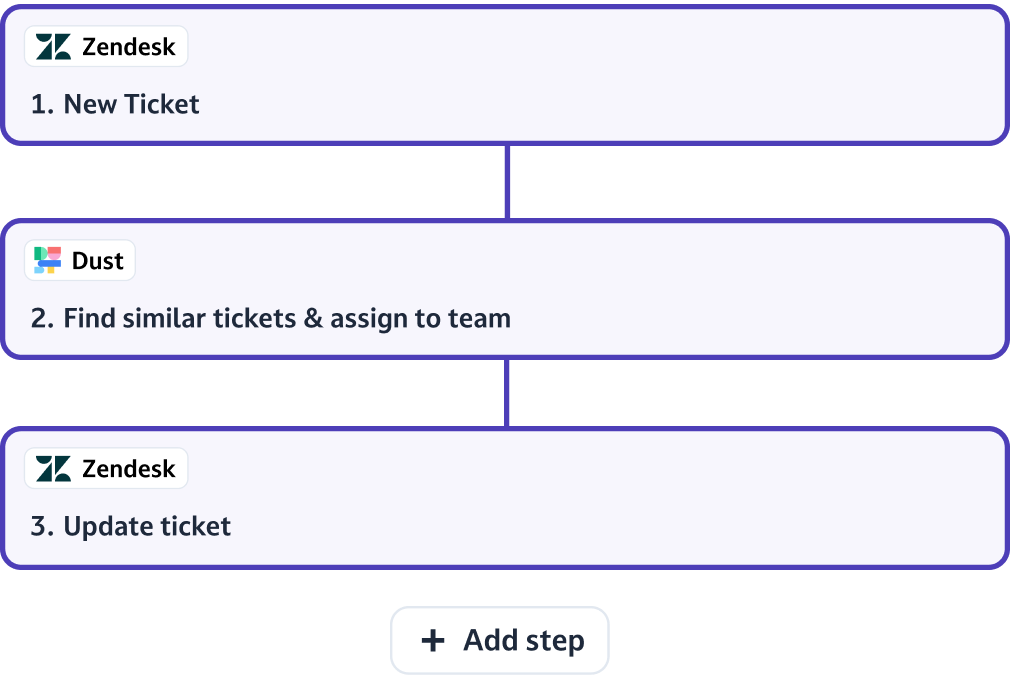
Add to workflows
Trigger AI actions via Zapier, Make, n8n or Slack workflows to automate tasks end-to-end.
Push further with custom code
Developer friendly platform designed to build custom actions and application orchestration to fit your team’s exact needs.
More about Dust’s Developer Platform
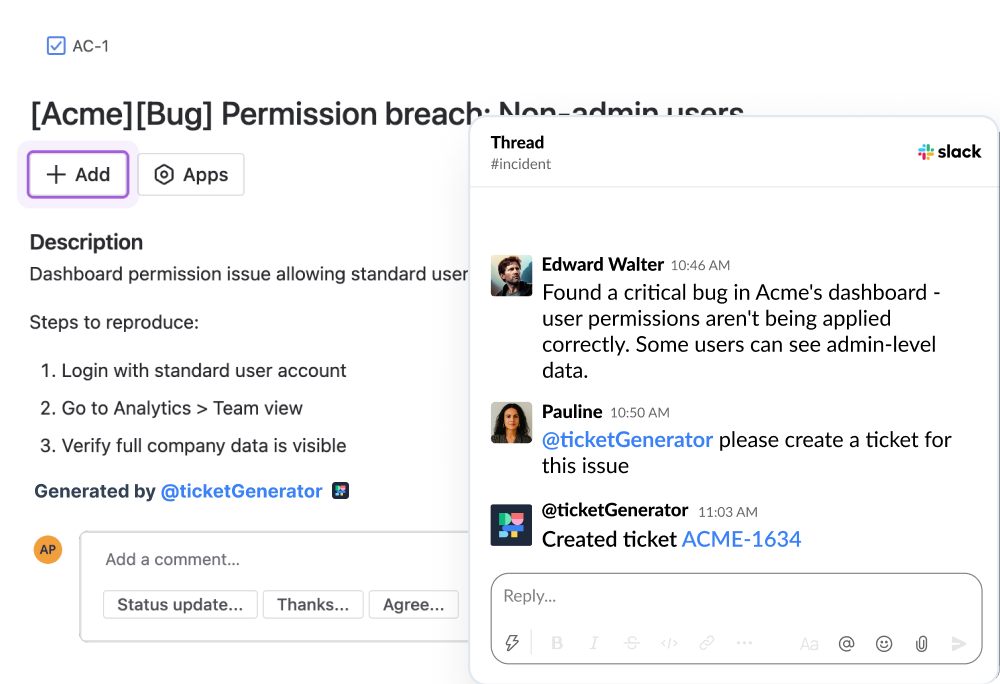
Build custom agentic tools
Develop advanced or agentic capabilities, from document auto-updates, triggered actions, or leveraging external APIs.
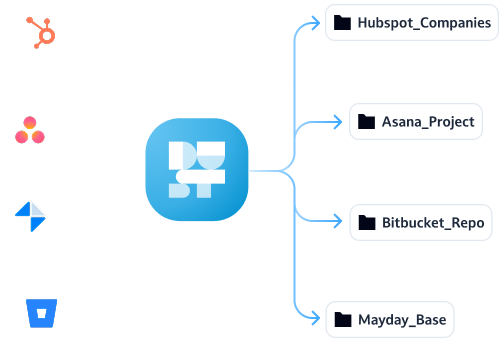
Build custom connections
No ceiling on data connections. Leverage the API to import in knowledge from any source and let agents tackle more ambitious use cases.
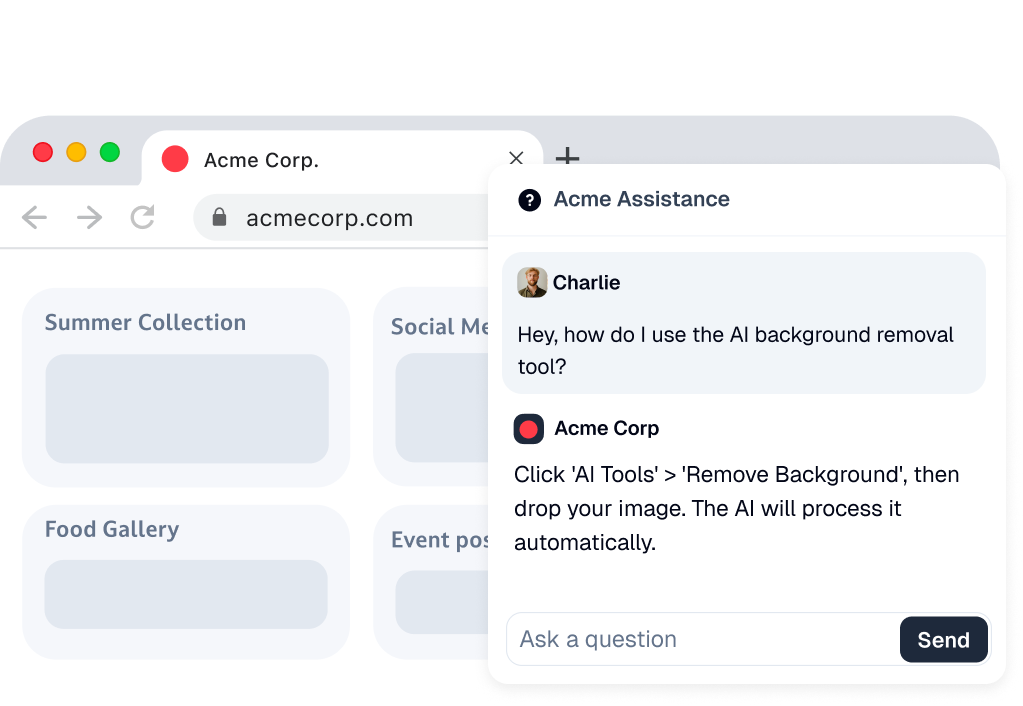
Build custom integrations
Use our API to embed agents in your apps or websites, unlocking fully custom user experiences and deep automation.
Built with enterprise-grade security
We've made security our core focus from day one to safeguard your company data and workspace privacy. Avoid shadow IT and benefit from Enterprise-level privacy from model providers. SOC2, HIPAA & GDPR compliant.
More about Security



Ingest data on your terms
Control data selection and hosting location within rigorous security parameters.



Select trusted models only
Pick from trusted providers with zero data retention nor model training.
Maintain rigorous access control
Tailor Dust's features to each user according to specified access rights.
Driving AI ROI together
Everett Berry
Head of GTM Engineering at Clay
Vincent Delagabbe
Software Engineer at Alan
Thomas Adhumeau
Chief Privacy Officer at Didomi
Boris Lipiainen
Chief Product and Technology Officer at Kyriba
Valentine Chelius
Head of Marketing at Fleet
Boris Lipiainen
Chief Product and Technology Officer at Kyriba
Vincent Delagabbe
Software Engineer at Alan
Anaïs Ghelfi
Head of Data Platform at Malt
Matthieu Birach
Chief People Officer at Doctolib